Security and Architecture
Overview
Availability of procurement services is essential for your purchasing team, users, and organization to run smoothly. Put simply: Our network and platform simply cannot be unavailable at any time.
ESG’s platform is built from the ground up to achieve maximum availability. With multiple layers of caching and redundancy, running on Amazon AWS, you can be sure our software agnostic “one-to-many” platform will be available at all times. Named as a Cloud Leader for the 10th Consecutive Year in Gartner’s Infrastructure & Platform Services Magic Quadrant, the AWS Cloud spans 57 Availability Zones within 19 Regions around the world, with announced plans for 12 more Availability Zones and four more Regions in Bahrain, Cape Town, Hong Kong SAR, and Stockholm. ESG makes full use of this resilience and reach to ensure seamless and reliable service for all our clients, all of the time.
Amazon Web Services as a Solid Foundation
As explained above, ESG running on AWS ensures a highly secure, scalable and availability of services for all our customers. Amazon have grown to become the dominant cloud service platform in the modern world. Every web-based solution needs to be hosted somewhere, so at ESG we have chosen the very best platform to support our growing customer base.
Data Security
Unless otherwise noted, client’s data are separated on different instances and databases. This is the ultimate level of data security in the cloud. This is enforced on several layers of the architecture, including authenticated sessions, which are required for any page access. Sessions are stored in cookies that do not include any other information than Session ID (session data is stored on server databases). Client ID is never transmitted or stored during page access, thus preventing ID spoofing. All sensible information, including personal information, bank accounts or authentications are stored encrypted in the database.
ESG includes many features to secure the user login that is passed transparently from the client’s existing ERP/accounting/procurement platform:
- Passwords are never kept cleared in ESG, and are hashed (one way encryption) using a very strong algorithm to prevent brute force attacks. The system first hashes the password that has been entered and then compares it with the hashed password stored in the database.
- ESG uses a mix of bcrypt encryption algorithm based on blowfish and sha1 proprietary salt to protect against rainbow table attacks. This adaptive over time algorithm remains resistant to brute force search attacks even when increasing computation power.
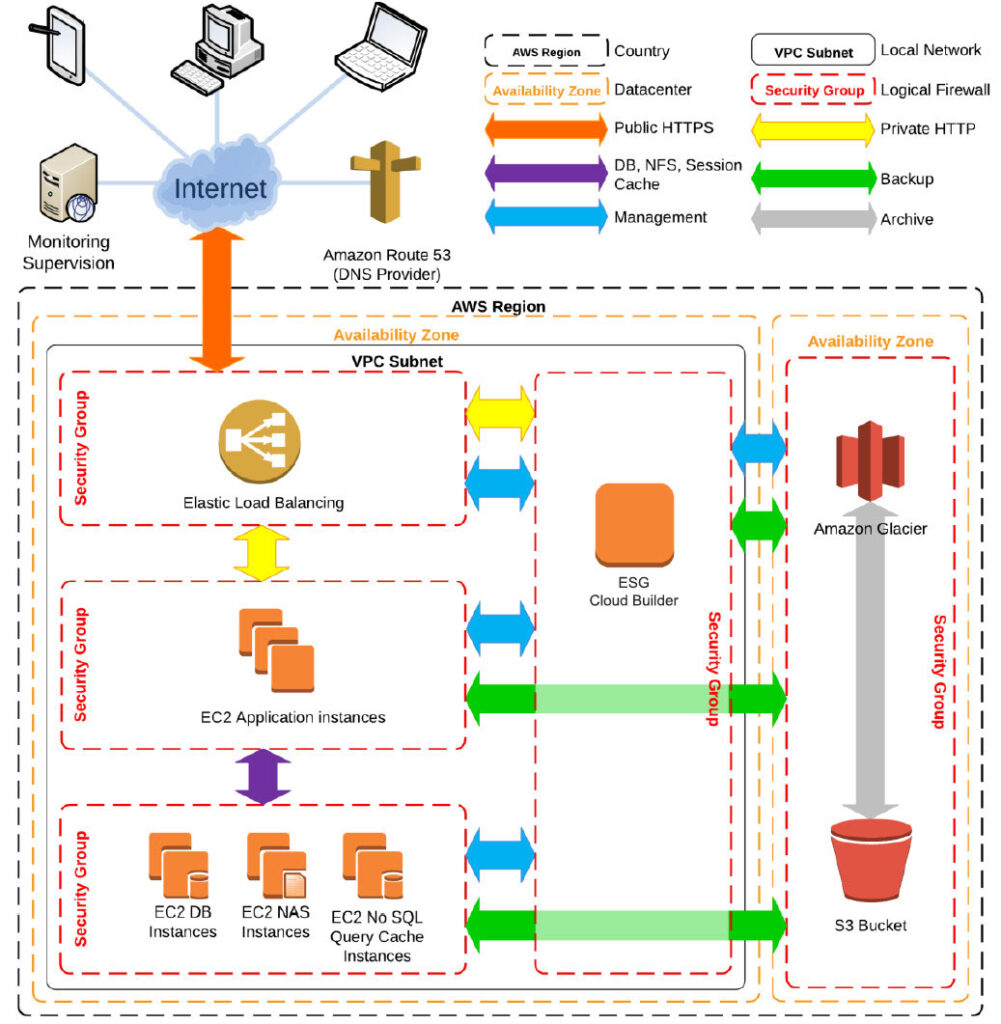
Architecture
Again, the ESG platform is using Amazon Web Services (AWS) private cloud solution. Access to the application is only possible using https and http protocols through a load balancer.
Standard Amazon Linux instances are used with full AWS integration, secure configuration and Amazon package repository access. These instances are based on Red Hat Enterprise Linux distribution. Weekly security updates are performed on all instances automatically. Relational databases are based on MySQL or MariaDB. MongDB is used as the NoSQL database to manage sessions, query cache and specific information.
To learn more about ESG’s security or architecture, or how we achieve any of the above, feel free to get in touch. We would be happy to arrange a call or webinar to explain more.